Malware or Viruses have been a danger which stalks computer users for long time ago. A whole system of a firm or even a group of companies can be destroyed because of only one infected computer.
Endpoint Detection and Response
Malware – The threats of all shapes and sizes
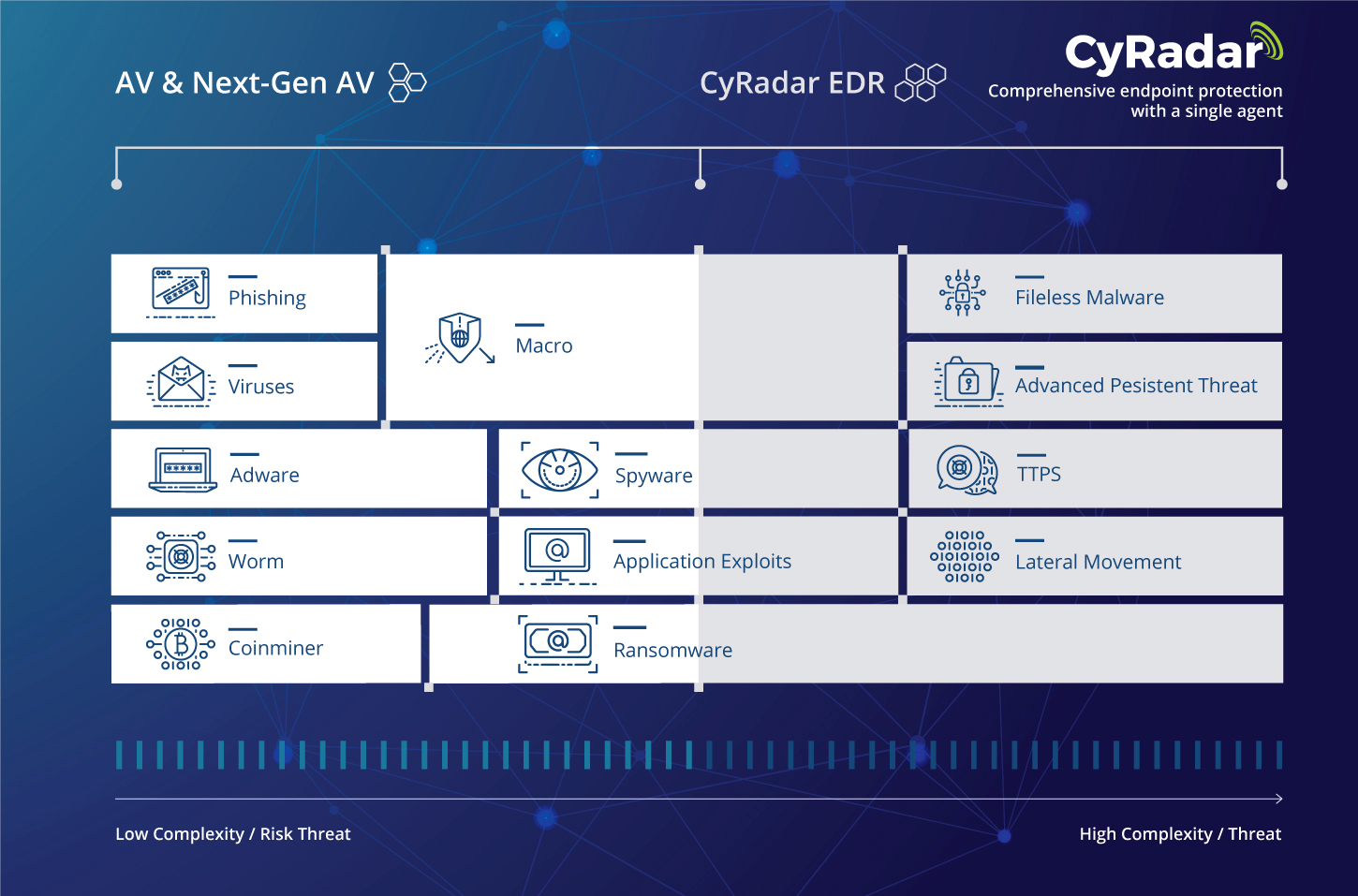
To be survivals, malware have been constantly changed making them difficult to be discovered. This is a challenge to traditional solution which focuses on signatures or significant behaviors. At this moment, a various of malware are silently doing harm to users without any notice. In some cases, malware can be identified but forensic investigation and infection cannot be found.
CyRadar EDR Solution
CyRadar EDR (CyRadar Endpoint Detection and Response) is the comprehensive next-gen antivirus which has ability to constantly monitor whole system, early detect potential threats; therefore, it sends warning and solve related issues. Finally, CyRadar EDR collects relevant information to forensic analysis and infection reason.
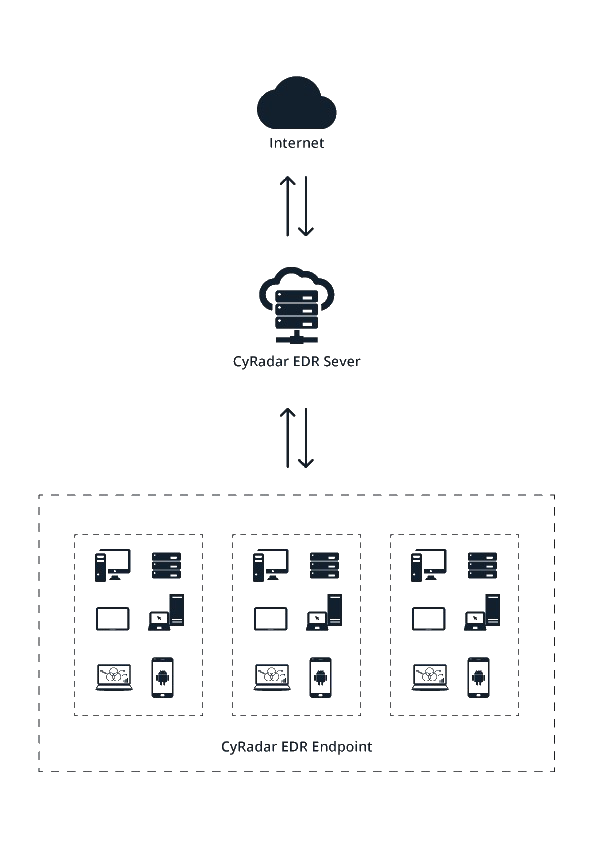
CyRadar EDR applies Big Data, Machine Learning, Sandbox… and works in model of client/server or known as unified centralized management. There is a server in center and clients which was installed CyRadar EDR Endpoint.
CyRadar EDR Server
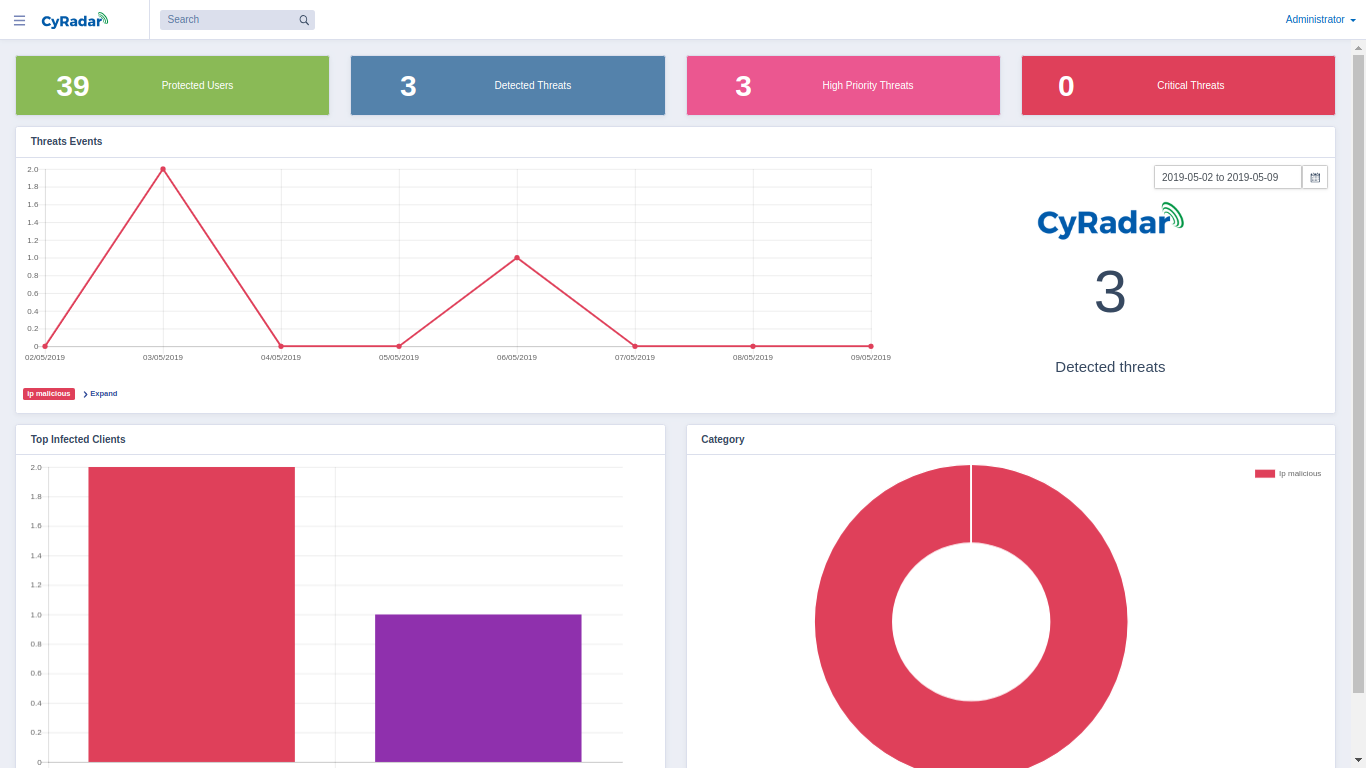
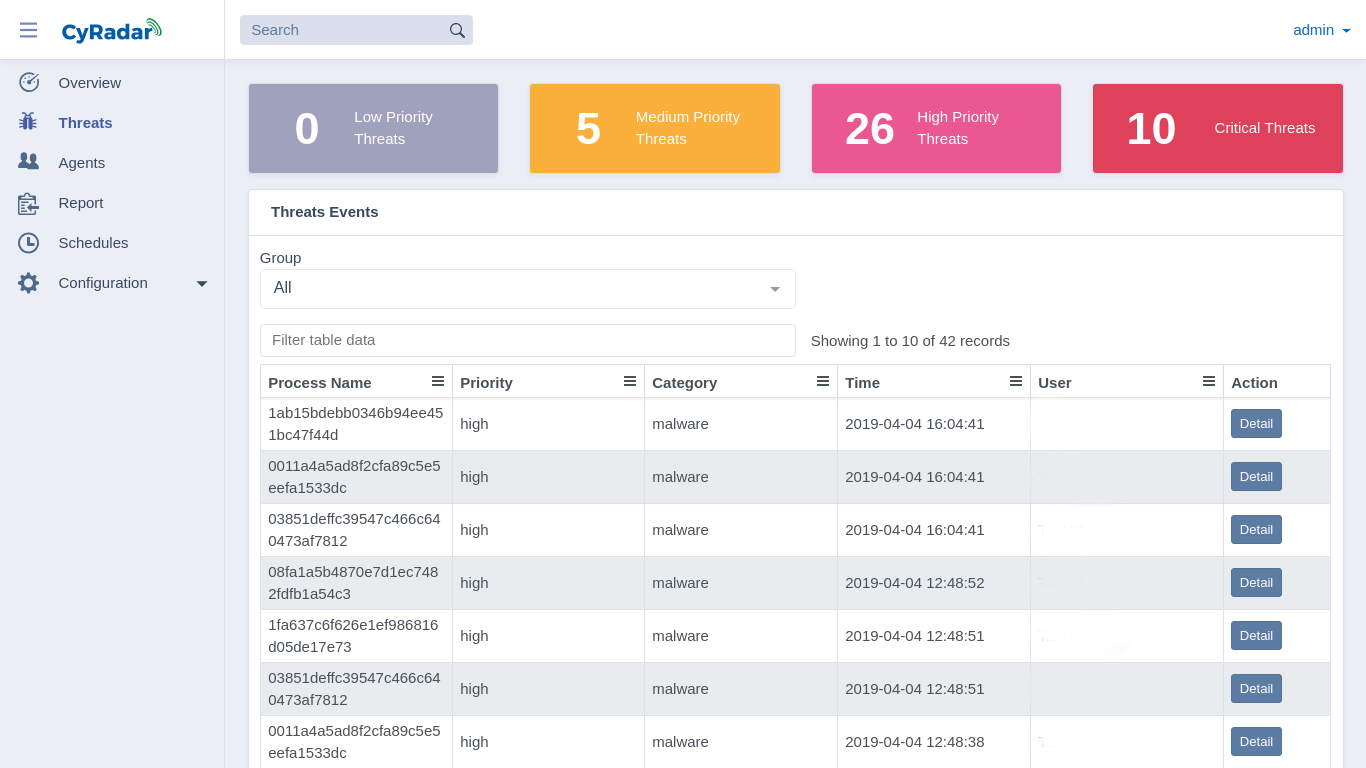
CyRadar EDR Server is the centralized management giving warnings, policies and orders for CyRadar EDR Endpoint. Through reports of log traffic and infection process, admin can evaluate and handling the issue.
CyRadar EDR Endpoint
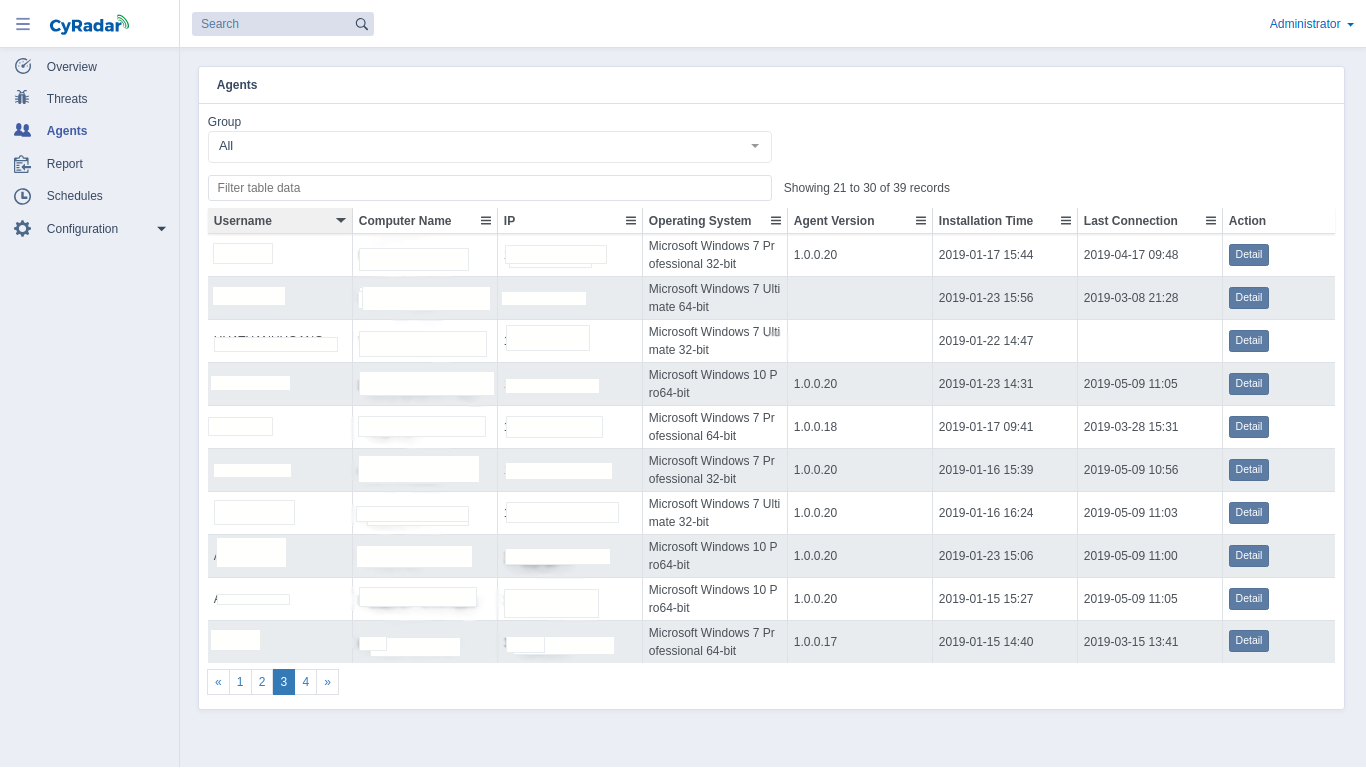
CyRadar EDR Endpoint in clients auto protects malware including trojan, spyware, adware as soon as they try to enter the computer. CyRadar EDR Endpoint deals with malicious code spread via USB, website, files, trojan and sends report to CyRadar EDR Server.
Comparison
Antivirus
Traditional antivirus solution
- Malwares detection bases primarily on Signature Files
- Only detection of already malwares
- Basic computer protection (isolation, file deleting)
- Incomplete information about malwares
- Passive operation, only detection appeared malwares
CyRadar EDR
CyRadar EDR Solution
- Malwares detection bases on Signatures and intelligent identification technology
- Ability to detect all malwares including newest ones, APTs, Fileless ...
- All process: Identify, prevent and fix
- Provide complete information about malwares used for investigation
- Constantly monitoring all process to early malicious code detection
How it works
EDR works by installing an agent on the end user device (CyRadar EDR Endpoint), which is used to continually monitor network events. These events are recorded to a central database (CyRadar EDR Server). EDR tools can then analyze the data to either investigate and identify a past incident or use the data to look for similar threats.
The data and analysis results on the server are confidential according to the configuration of the operating user. Depending on needs, the user can share this malicious analysis data to other centralized sources according to a certain protocol. In the case of data sharing protocols that have specific characteristics, but with specific structural specifications, CyRadar can fully support the development of integration of such protocols according to customer requirements.
Main components
1. Detection
Synthesis of small modules to serve the monitoring, forecasting and early detection of risks
2. Processing
Based on the analysis results, the program performs appropriate and integrity handling (warning, prevention, isolation, removal). The removal step will be done thoroughly, completely removing the remnants of malicious code from the machine (Delete files, startup components, registry ...)
3. Investigation
Summarizing and sequencing related event information, visualizing event flows, helping users easily identify the route of infection as well as the time when malware enters the machine
Outstanding features
1. Advanced persistent threat prevention (APT)
Not only identify and handling signatures virus, CyRadar EDR also applies AI; Malware Graph to early detect APT
2. Quick response
Combining innovative technology (Machine Learning, Sandboxing...) CyRadar EDR provides an organization with endpoint visibility through collecting data from endpoint devices, and then uses that data to detect and respond to potential outside threats
3. Forensic Analysis
Summarizing and sequencing related event information to provide objective overview as well as easier specify infected way
4. 24/7 Support Services
CyRadar’s support service is available 24/7
5. Report
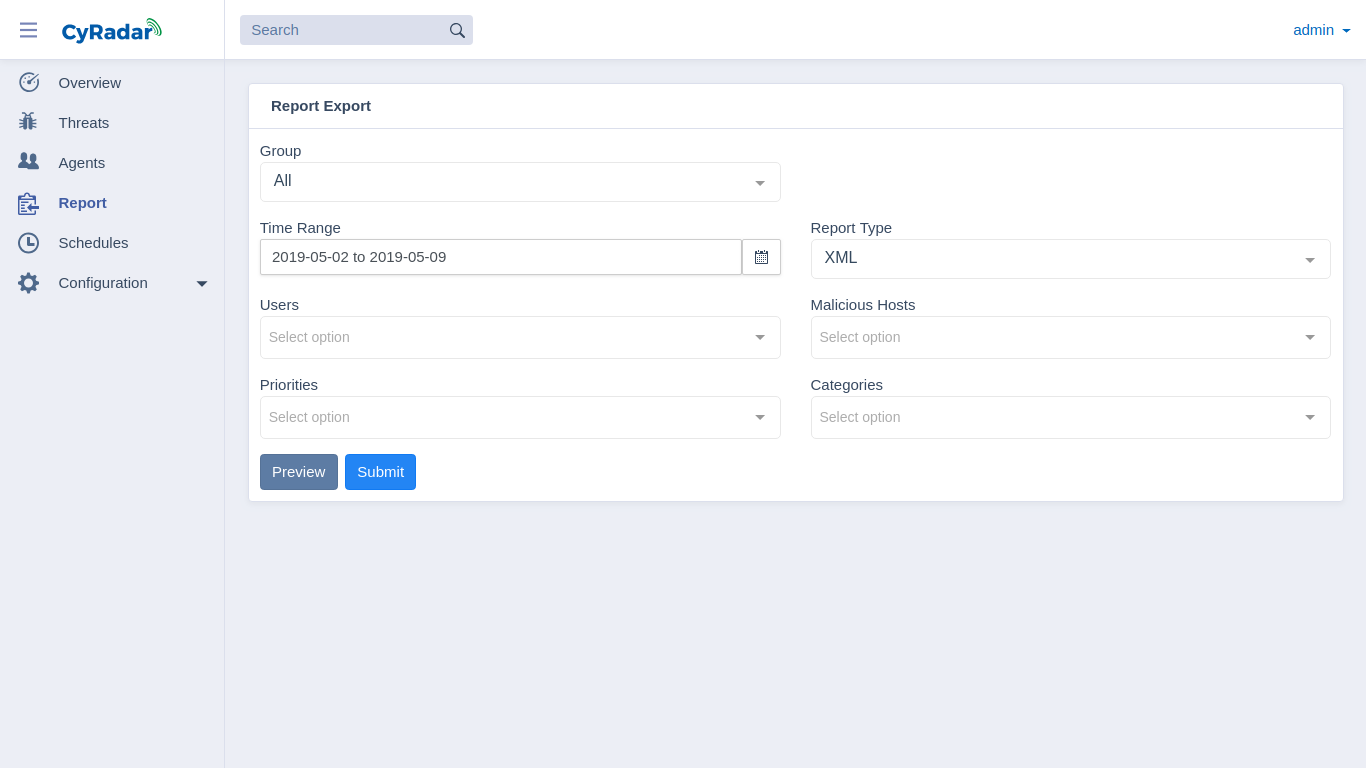
Periodical report, real-time report and potential risk report